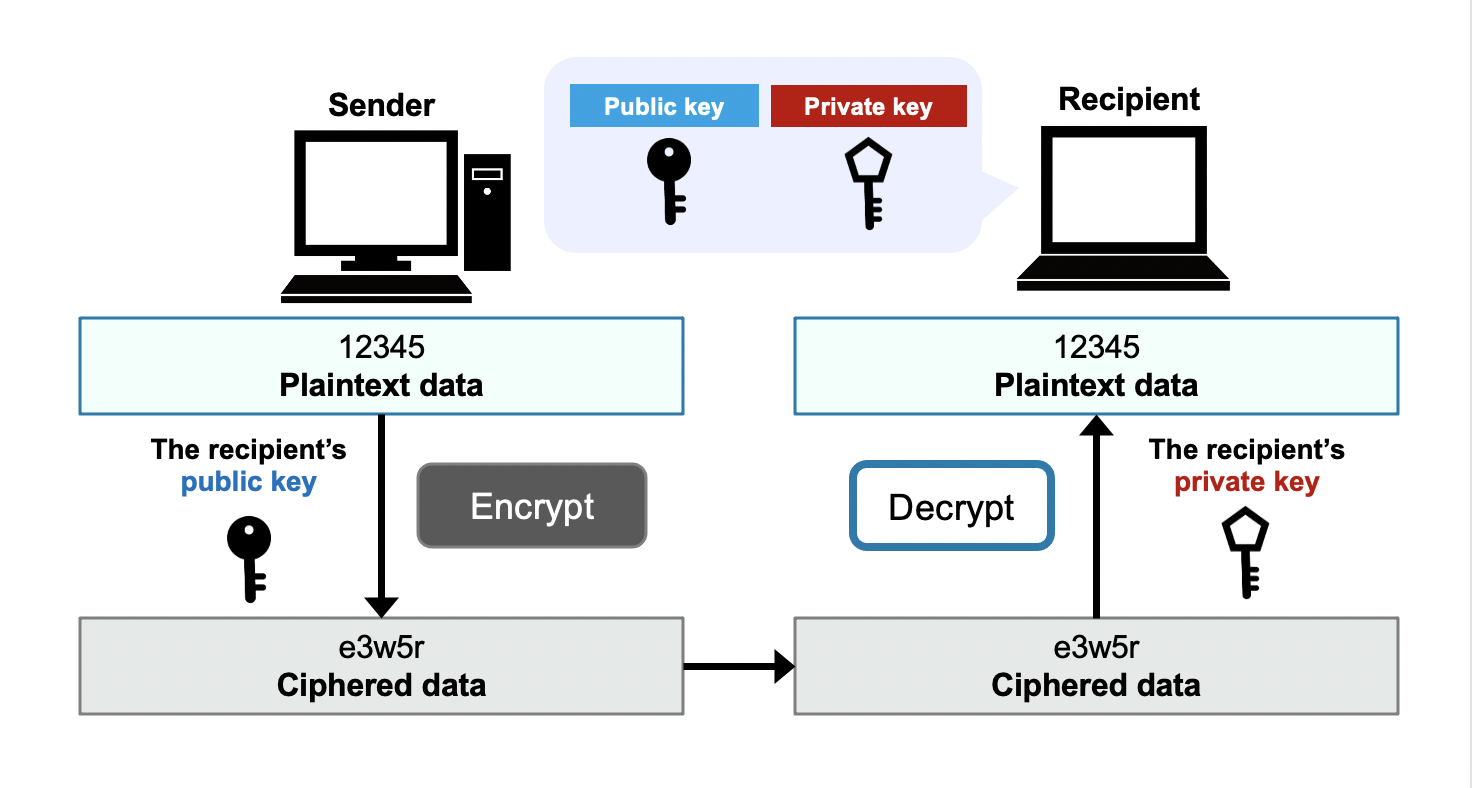
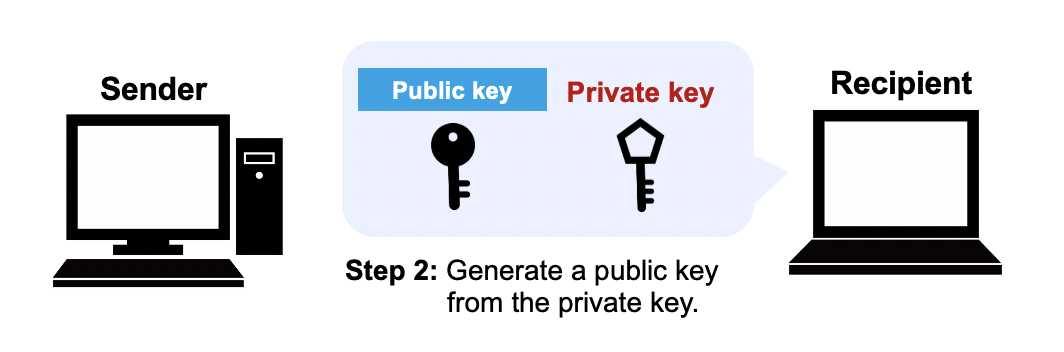
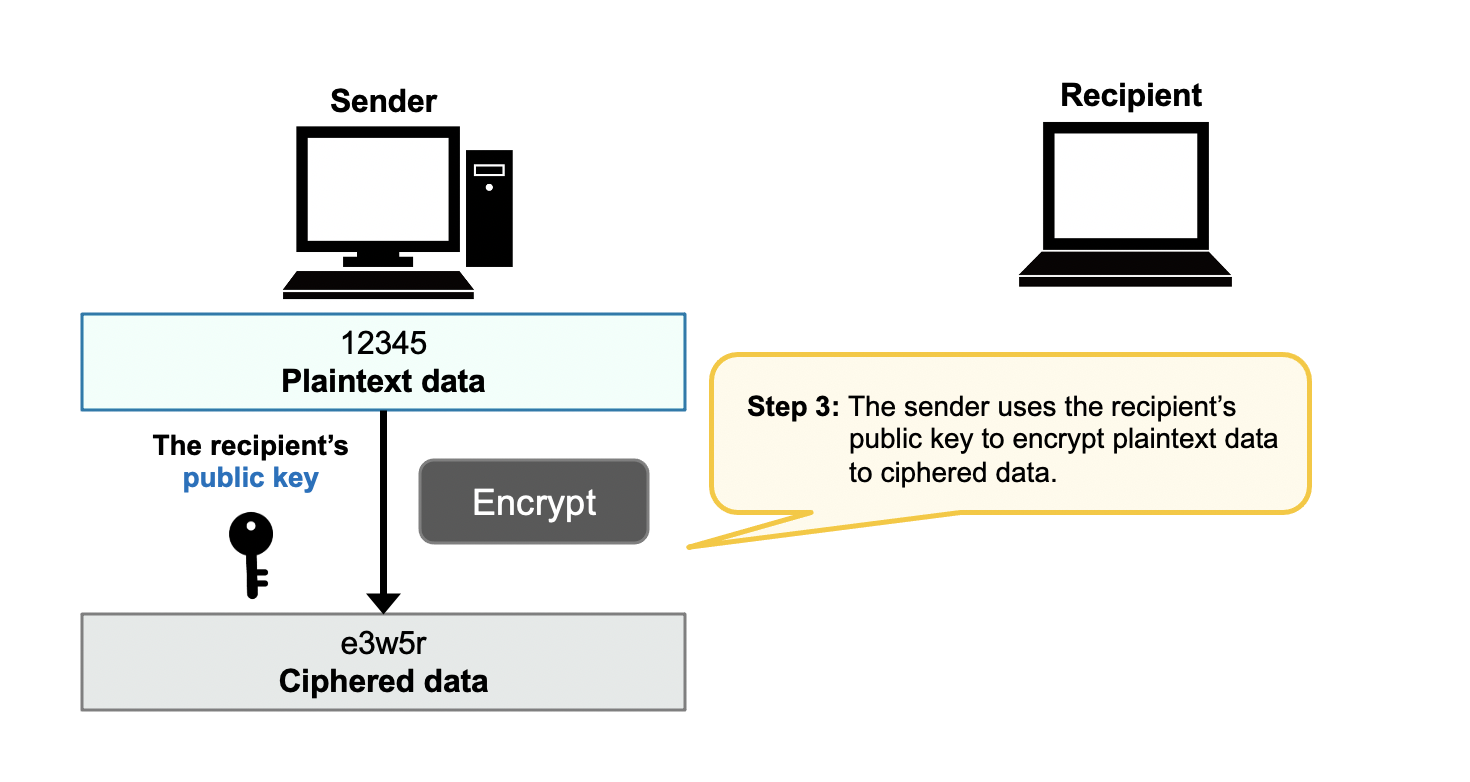
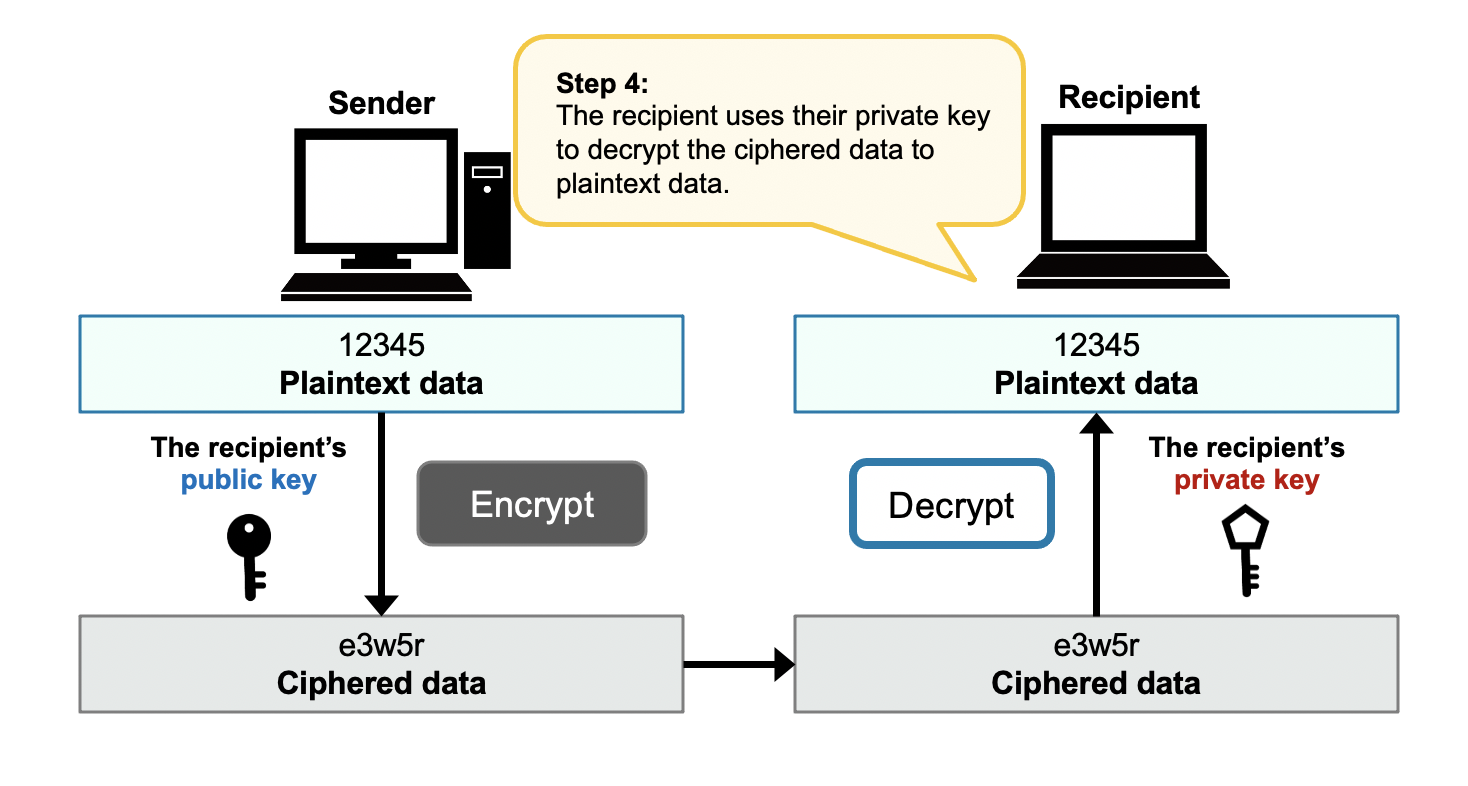
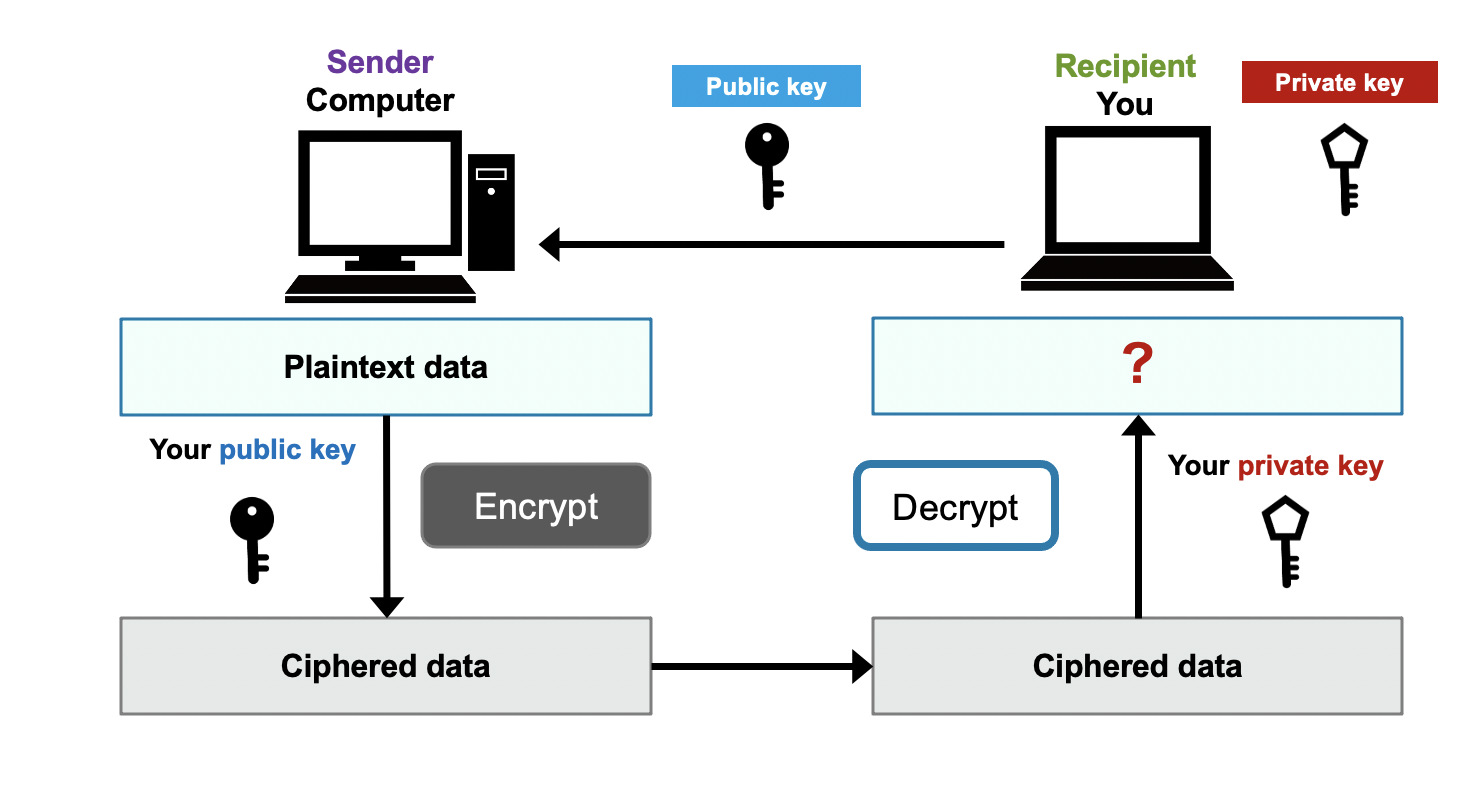
In the public-key cryptography, a recipient prepares a pair of public and private keys.
Encrypted message by the public key can only be decrypted by the pair private key.
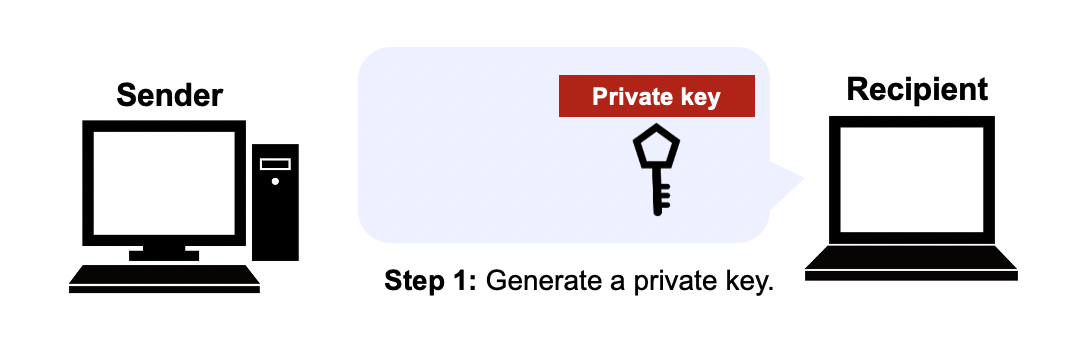
At first you play a role as a 'recipient' and create a private key. Click the following button and a private key will be created.
Notice: The private key file doesn't need to be opened with any appication program on your computer. After downloading the file move to the next step.
(Especially be care for mac users. Safari on Mac may open the downloaded '***.key' file with Keynote app automatically. At that case just close the keynote window soon.)
- Click "Create a private key" button.
- Download the file named 'private.key'. Confirm where you saved the file (maybe "Download" folder by default).
If your machine opened the file associated with the extend '.key' (especially Keynote on MacOS), terminate the app soon. This exercise doesn't need any app installed on your machine.